PlAwAnSaI
Administrator
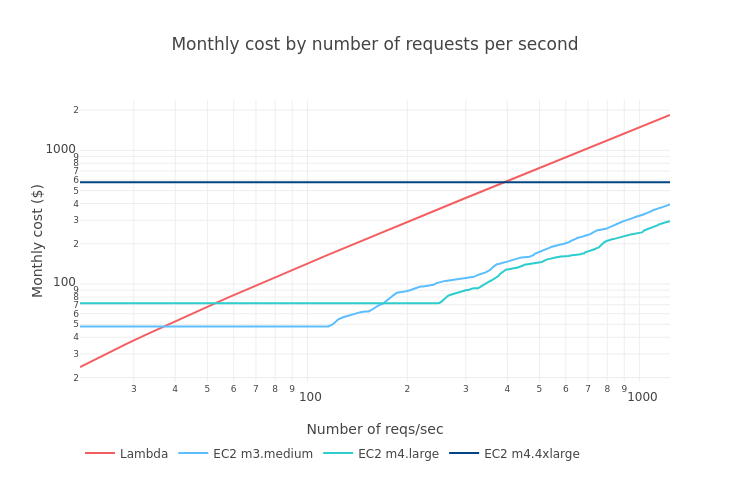
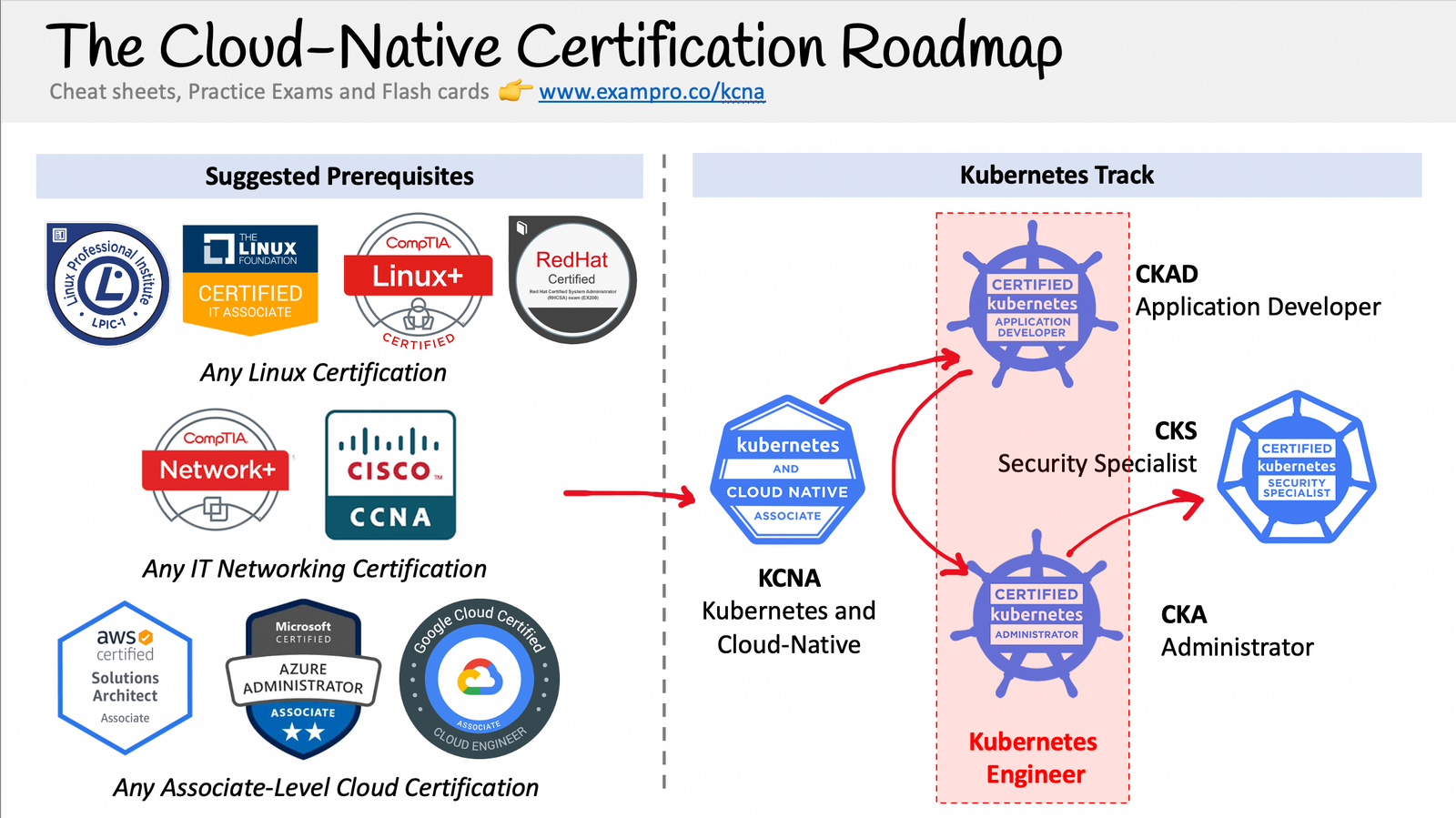
- The Cloud-Native Certification Roadmap:
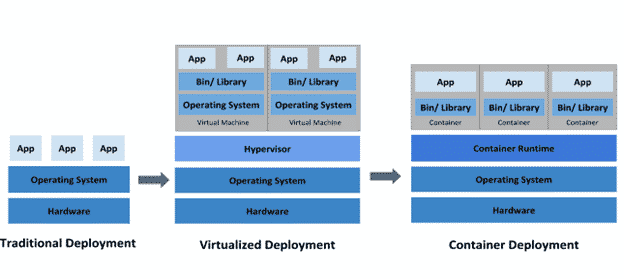
- รู้จัก Container มันคืออะไร แตกต่างจาก Virtualization อย่างไร:
www.blognone.com/node/105928
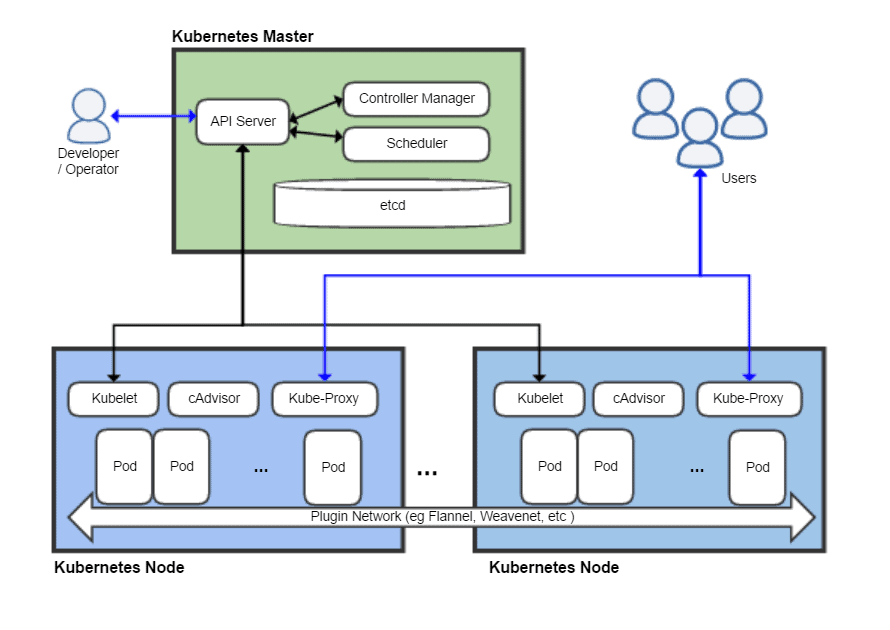
- Kubernetes คืออะไร ทำไม Orchestration จึงเป็นหัวใจของ Infrastructure ยุคนี้:
www.blognone.com/node/106492 - Certified Calico Operator: Level 1 - Learn Kubernetes networking and security fundamentals using Calico Free!
academy.tigera.io/course/certified-calico-operator-level-1 - Which Kubernetes Certification Path Should I Take?:
acloudguru.com/blog/engineering/which-kubernetes-certification-path-should-i-take - Kubernetes 101:
www.youtube.com/watch?v=GPC6mEuiBBE - Kubernetes for Beginner:
medium.com/@sikiryl/ep-0-kubernetes-content-e138c25846bb - https://www.proen.cloud

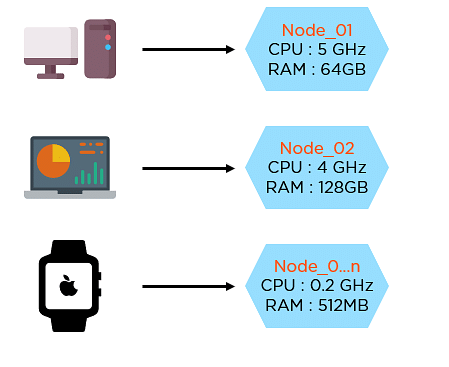
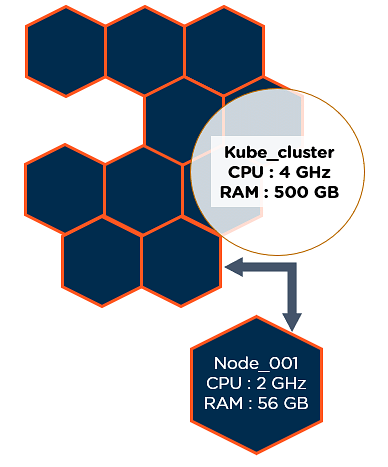
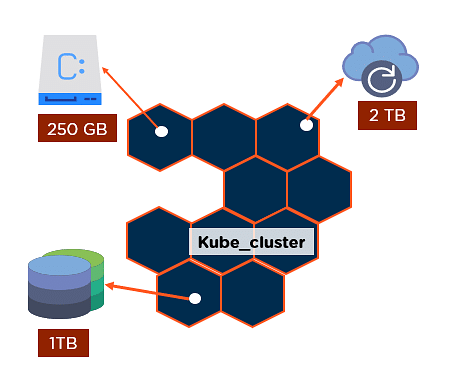
- IP per Pod -> VMs & Processes ≈ Pods & Containers
- Isolation with Network Policy -> simple 'flat' network

- Host Local IPAM CNI Plugin
- Other CNI Plugins
- Network Policy
- Performance & Encryption

- Example service: my-svc.my-namespace.svc.cluster-domain.example
- Pod in cluster: my-svc.my-namespace
- Pod in my-namespace: my-svc

- Pod IPs may not be routable outside of the cluster (e.g. overlay network)
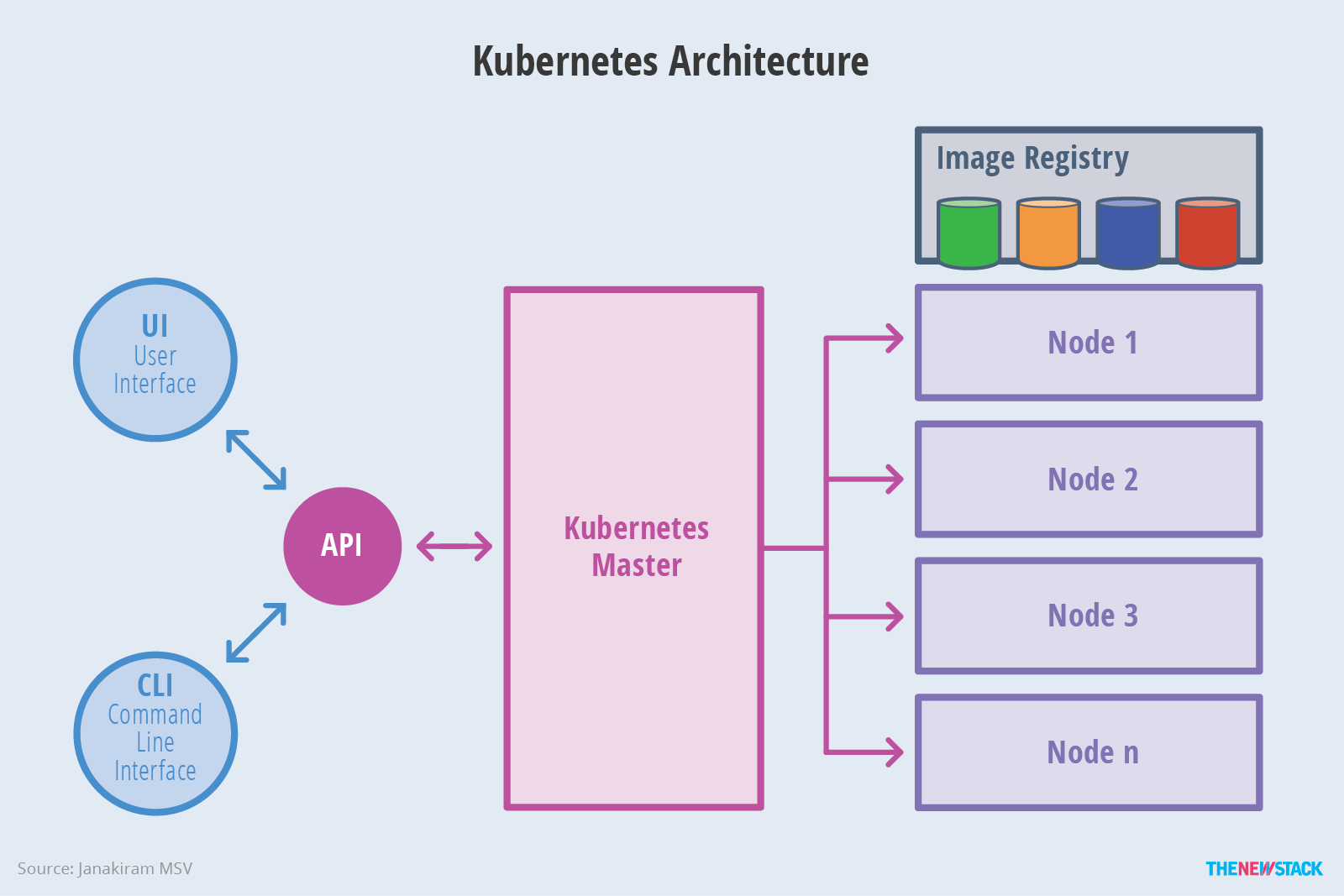
- The key principles of the Kubernetes networking model:
- Every pod gets its own IP address
- Containers within a pod share the pod IP address and can communicate freely with each other
- Pods can communicate with each other directly without NAT
- Network isolation is provided by network policy
- The Kubernetes network model requires L3 (IP) connectivity only. Pods may be in the same CIDR, but are normally not strictly in the same subnet as they don't have L2 connectivity.
- Kubernetes supports overlay and non-overlay networks.
- The Kubernetes network model does not require that pods can communicate with workloads outside of the cluster without NAT. For example, if the pod network is an overlay, then it needs to NAT outgoing traffic.
- Kubernetes supports network plugins using CNI API.
- Kubenet built into Kubernetes and can provide some very basic networking, but is not an API used by Kubernetes network plugins.
- Network plugins can implement IP Address Management, but IPAM is not an API.
- Kubernetes supports a REST API for managing Kubernetes resources, but uses a different API for network plugins.
- Kubernetes Services:
- Can be though of as a virtual load balancer built into the pod network
- Normally use label selectors to define which pods belong to a Service
- Are discoverable by pods through the Kubernetes DNS service
- May include external load balancer
- The Kubernetes network model does specify that pods can communicate with each other directly without NAT. But a pod communicating with another pod via a service is not direct communication, and normally will use NAT to change the connection destination from the service to the backing pod as part of load balancing.
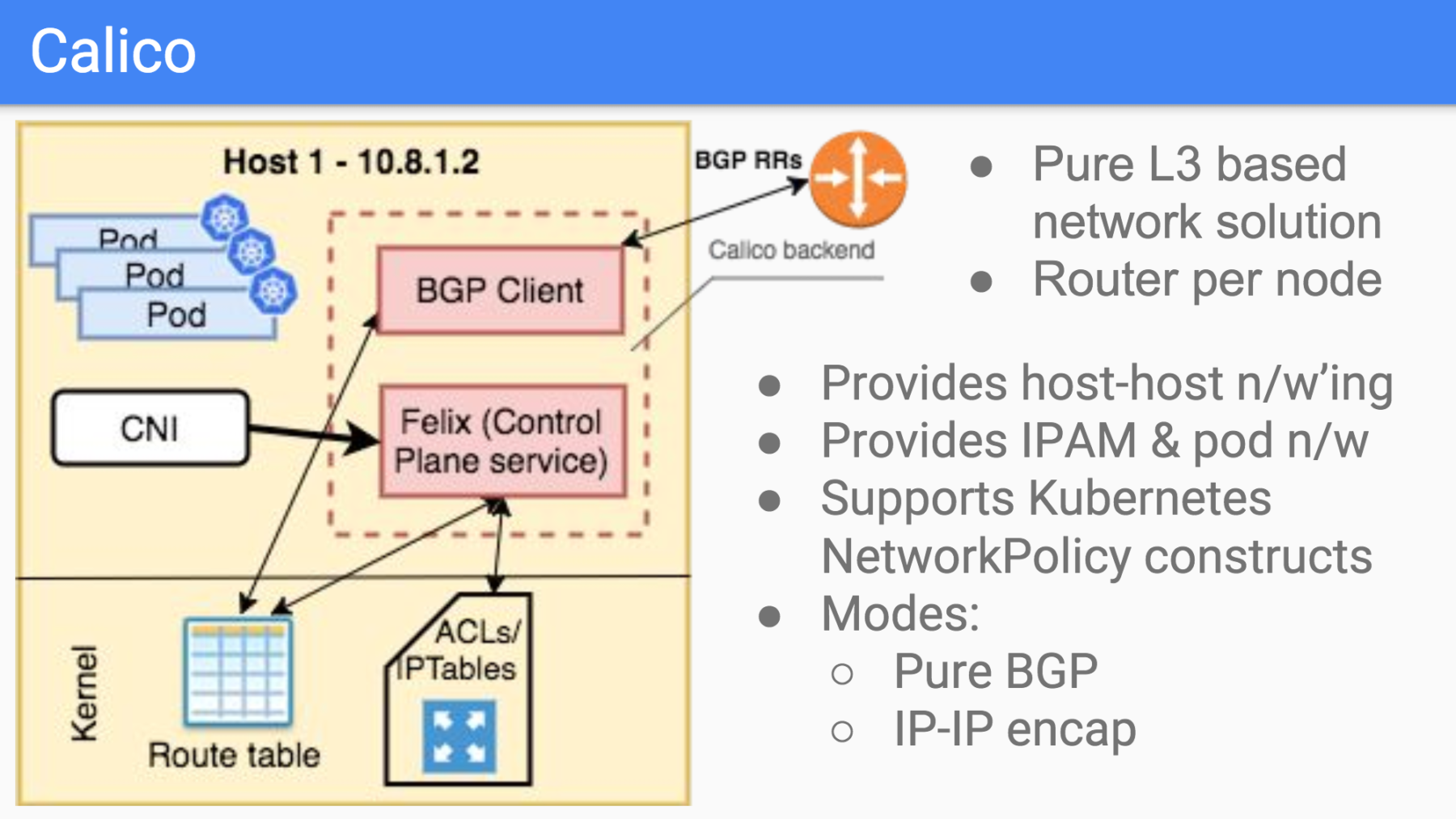
- Calico can be installed:
- As part of hosted Kubernetes platform (e.g. Amazon Elastic Kubernetes Service (AWS EKS), Azure (AKS), Google Engine (GKE), IBM Cloud (IKS))
- As part of a kubernetes distro or installer (eg. kops, kubespray, micro8s, etc.)
- Using YAML manifests
- Using the Tigera Calico operator

- Simple 'flat' network
- Isolation is not defined by the structure of the network
- Attacks continue to grow in sophisticated and volume
- Traditional firewalls struggle with dynamic nature of Kubernetes
- Network Policy is label selector based -> inherently dynamic
- Empowers teams to adopt 'shift left' security practices
- apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: blue-policy
namespace: production
spec:
podSelector:
matchLabels:
color: blue
ingress:
- from:
- podSelector:
matchLabels:
color: red
ports:
- port: 80 - apiVersion: projectcalico.org/v3
kind: NetworkPolicy
metadata:
name: blue-policy
namespace: production
spec:
selector: color == 'blue'
ingress:
- action: Allow
protocol: TCP
source:
selector: color == 'red'
destination:
ports:
- port: 80
Last edited: