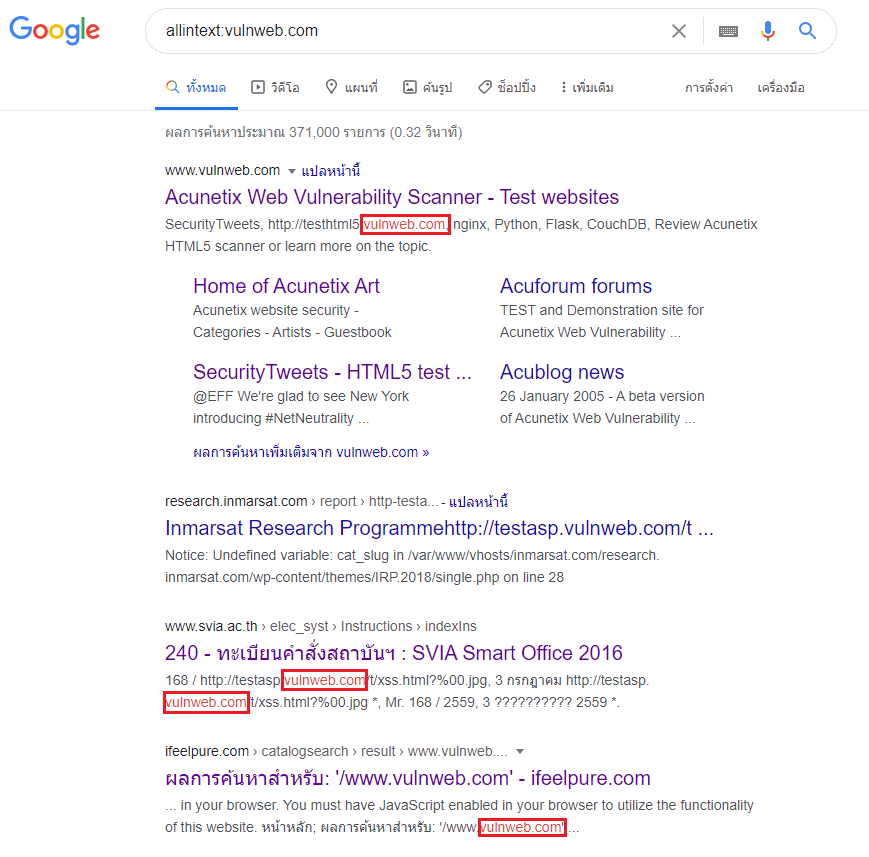
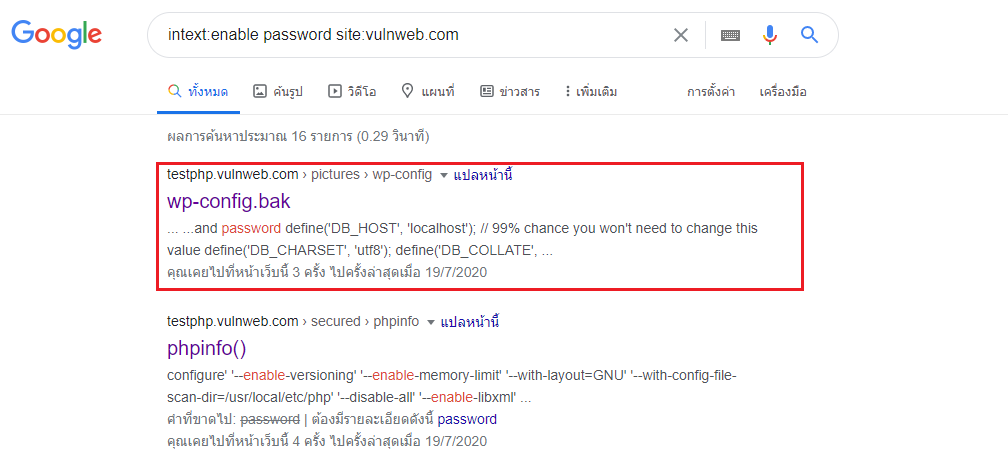
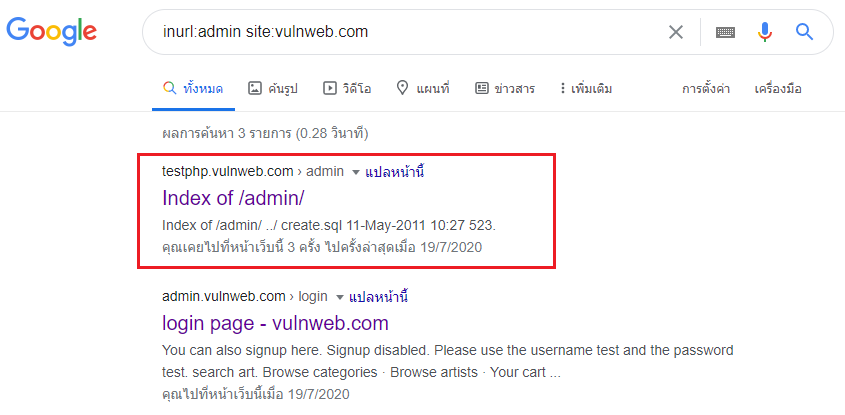
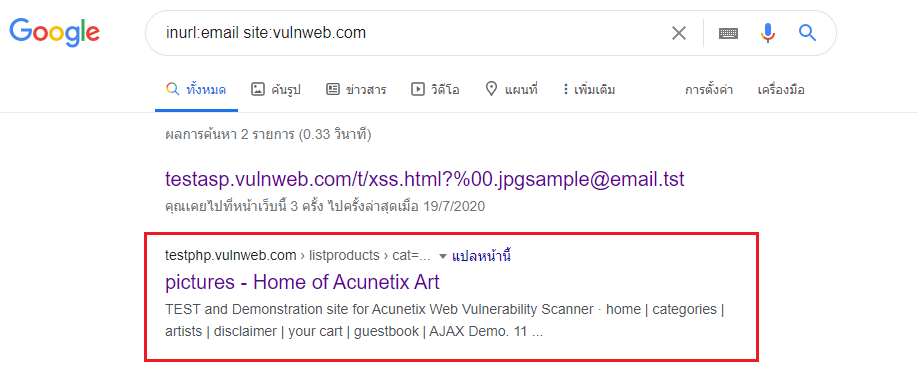
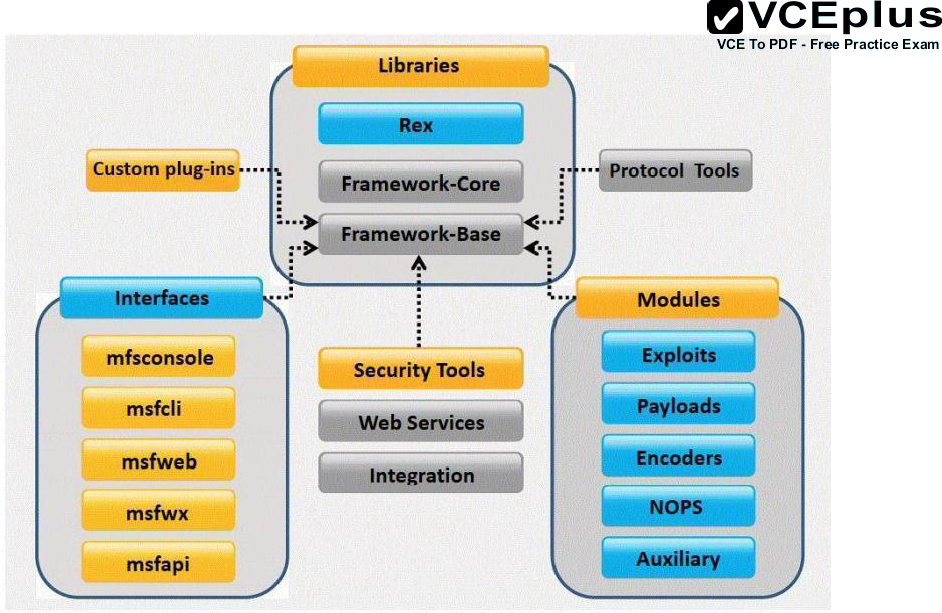
Foundations of EC-council and CEH (Certified Ethical Hacker):www.eccouncil.org/about
The Importance of Ethics:www.eccouncil.org/code-of-ethicscert.eccouncil.org/code-of-ethics.html
Getting Certified:www.eccouncil.org/programs/certified-ethical-hacker-ceh
Exam Topics/Blue Print:cert.eccouncil.org/certified-ethical-hacker.html
Getting permission from the owner is the most important aspect of scoping when it comes to security testing.Without permission, testing is unethical and potentially illegal.
EC-Council was created to ensure certify security professionals had a minimum level of knowledge.
There is no set passing score for the CEH.The passing score varies from one test to the next.
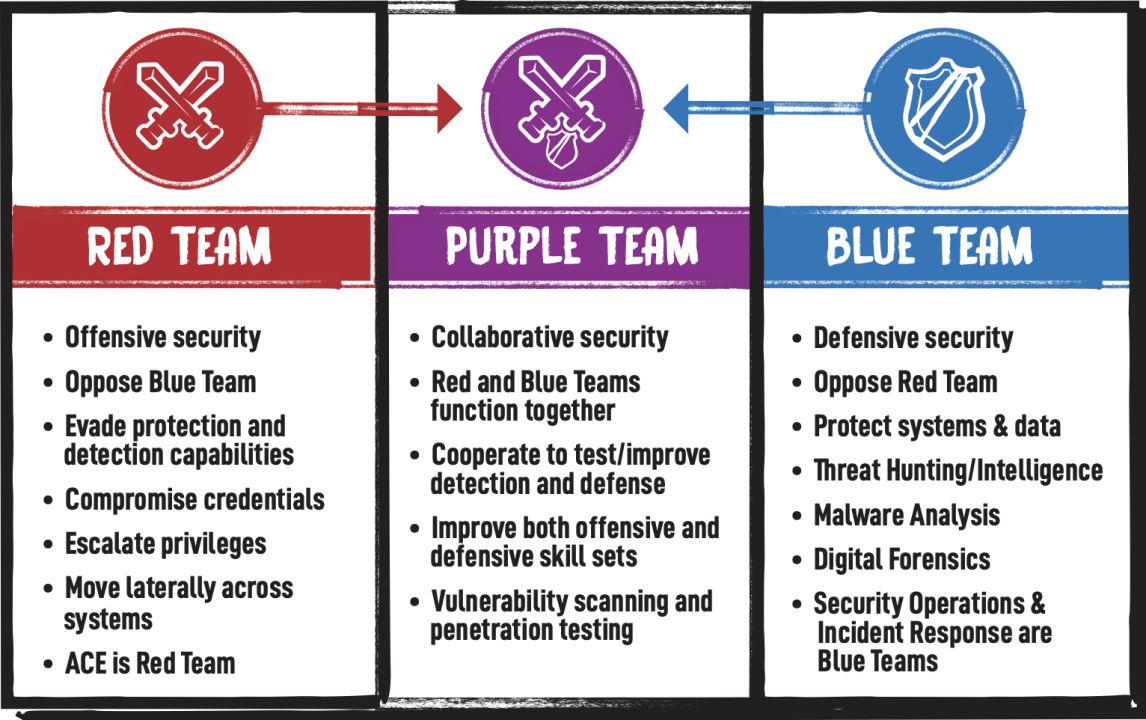
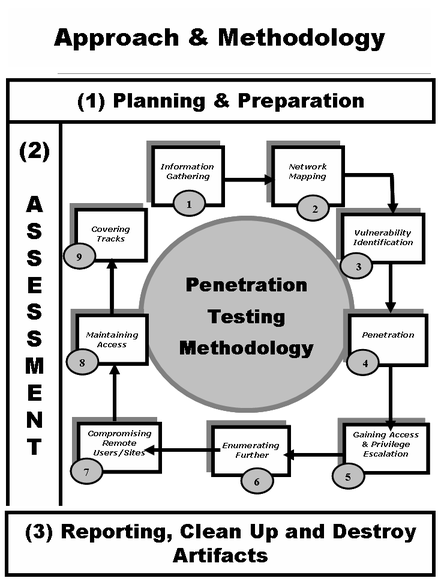
The purpose of ethical hacking is to improve the overall security posture of companies/organizations by pointing out flaws in their technical controls before they can be exploited.
EC-Council requires 2 years of experience you need to have before you can attempting/take the exam if you don't take the boot-camp training.
Background:
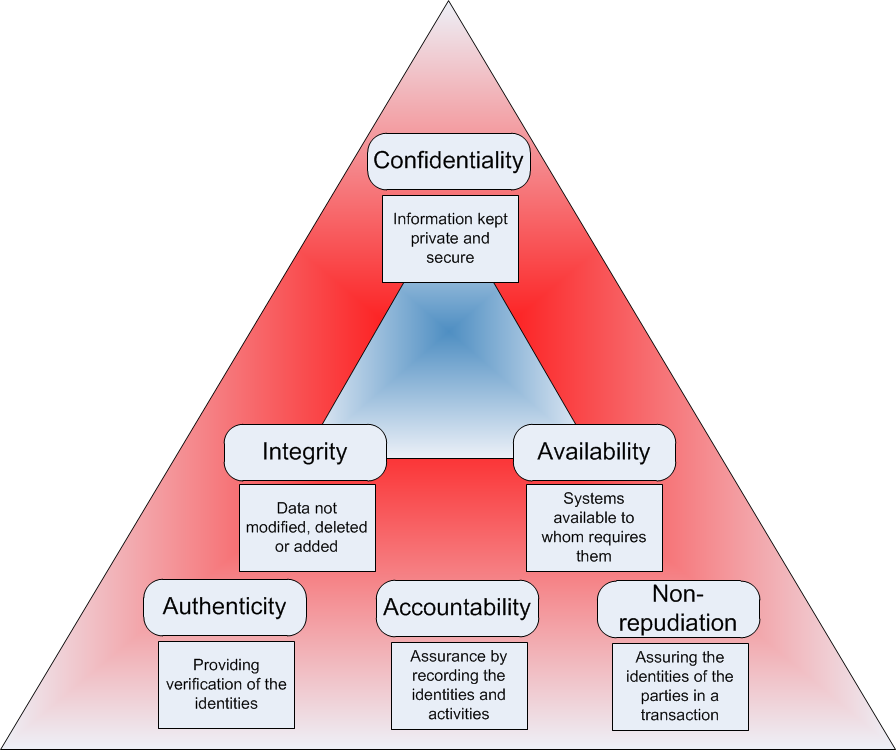
The CIA Triad:
ส่วนประกอบหนึ่งของ INFOSEC (Information Security) ซึ่งมาจากคำว่า Confidentiality (การรักษาความลับของข้อมูล), Integrity (ความแท้จริงของข้อมูล) และ Availability (การใช้งานได้ของระบบ) ซึ่งเป็นสิ่งที่ Security Professional ต้องรู้และสามารถอธิบายได้
พื้นฐานที่จำเป็นสำหรับ 'Information Security Professional':www.acisonline.net/?p=1340
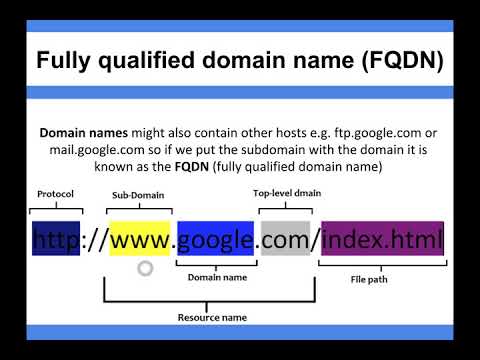
Data Communication and Networks - การสื่อสารข้อมูลและเครือข่าย Computer & Network Topology:edu.bsru.ac.th/images/204/1211206/Chapter2.pdf
Communications Models:
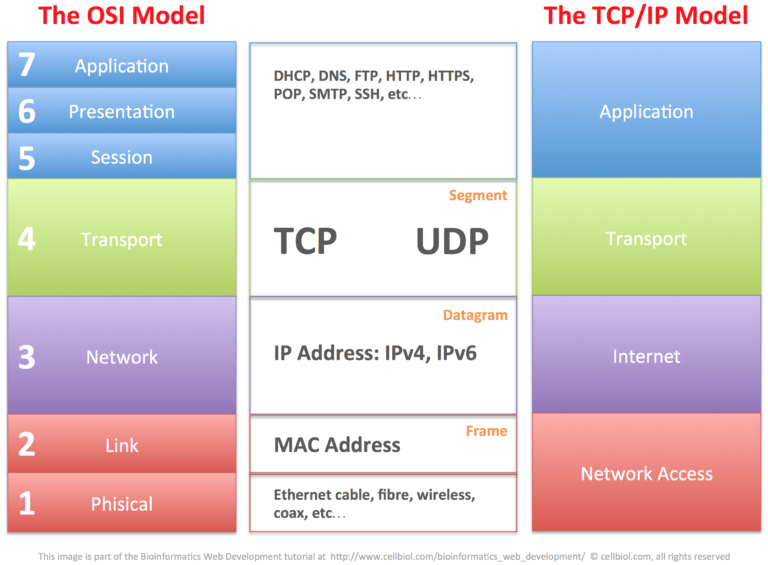
มาทำความรู้จักกับ OSI Model 7 Layers กันดีกว่า !!:netprime-system.com/osi-model-7-layers
en.wikipedia.org/wiki/Internet_protocol_suite
What are Ethernet, IP, and TCP Headers in Wireshark Captures:networkstatic.net/what-are-ethernet-ip-and-tcp-headers-in-wireshark-captures
Technique การคำนวณ IP Address:www.jodoi.com/book/book_technic_cal_IP.pdf
Have been given an IP address block, 192.168.15.0/24. Need to create subnets that can support as many as 25 hosts. 8 networks can create and The CIDR notation for each of those network is /27. 192.168.15.0-31, 192.168.86.32-63, 192.168.15.64-95,
192.168.15.96-127, 192.168.15.128-159, 192.168.15.160-191,
192.168.15.192-223, 192.168.15.224-255.
IPv6 Trace Analysis using Wireshark:sharkfestus.wireshark.org/sharkfest.13/presentations/PA-13_IPv6-Trace-Analysis-Using-Wireshark_Nalini-Elkins.pdf
http://www.thaicpe.com/discussion/1163/internet-protocol-version-6-ipv6
Exploring UDP (User Datagram Protocol):maxwellsullivan.wordpress.com/2013/03/12/wireshark-lab-5-exploring-udp
Exploring TCP (Transmission Control Protocol):maxwellsullivan.wordpress.com/2013/03/11/wireshark-lab-4-exploring-tcp
medium.com/@panupong.simto/คุยเรื่อง-tcp-protocol-แบบ-ยาวไป-ยาวไป-ตอนที่-1-2fa601197076
What is a Firewall?:
A firewall is hardware, software, or a combination of both that is used to prevent unauthorized programs or Internet users from accessing a private network and/or a single computer
A firewall:
- Acts as a security gateway between two networks
- Tracks and controls network communications - Decides whether to pass, reject, encrypt, or log communications (Access Control)
Hardware Firewalls:
- Protect an entire network
- Implemented on the router level
- Usually more expensive, harder to configure
Software Firewalls:
- Protect a single computer
- Usually less expensive, easier to configure
Stage of Evolution of Firewalls

acket Filter > Application Proxy > Stateful Inspection
Packet Filter:
- Packets examined at the network layer
- Useful 'first line' of defense - commonly deployed on routers
- Simple accept or reject decision model
- No awareness of higher protocol layers
- Simplest of components
- Uses transport-layer information only:
- IP Source Address, Destination Address
- Protocol/Next Header (TCP, UDP, ICMP, etc.)
- TCP or UDP source & destination ports
- TCP Flags (SYN, ACK, FIN, RST, PSH, etc.)
- ICMP message type
- Examples:
- DNS uses port 53 - No incoming port 53 packets except known trusted servers
How to Configure a Packet Filter:
- Start with a security policy
- Specify allowable packets in terms of logical expressions on packet fields
- Rewrite expressions in syntax supported by your vendor
- General rules - least privilege
- All that is not expressly permitted is prohibited
- If you do not need it, eliminate it
Packet Filter Configuration:
Every rule-set is followed by an implicit rule reading like this.