Code:
Router# <span style="color: Black; font-style: normal; font-weight: bold">show ip route<br />
</span>
Code:
Codes: R - RIP derived, O - OSPF derived,<br />
Code:
C - connected, S - static, B - BGP derived,<br />
Code:
* - candidate default route, IA - OSPF inter area route,<br />
Code:
i - IS-IS derived, ia - IS-IS, U - per-user static route,<br />
Code:
o - on-demand routing, M - mobile, P - periodic downloaded static route,<br />
Code:
D - EIGRP, EX - EIGRP external, E1 - OSPF external type 1 route,<br />
Code:
E2 - OSPF external type 2 route, N1 - OSPF NSSA external type 1 route,<br />
Code:
N2 - OSPF NSSA external type 2 route<br />
Code:
Gateway of last resort is 10.119.254.240 to network 10.140.0.0<br />
Code:
O E2 10.110.0.0 [160/5] via 10.119.254.6, 0:01:00, Ethernet2<br />
Code:
E 10.67.10.0 [200/128] via 10.119.254.244, 0:02:22, Ethernet2<br><br>O:<br>Indicates the protocol that derived the route. It can be one of the following values:<br>
- B - BGP derived
- C - connected
- D - Enhanced Interior Gateway Routing Protocol (EIGRP)
- EX - EIGRP external
- H - NHRP
- i - IS-IS derived
- ia - IS-IS
- L - local
- M - mobile
- O - Open Shortest Path First (OSPF) derived
- P - periodic downloaded static route
- R - Routing Information Protocol (RIP) derived
- S - static
- U - per-user static route
- o - on-demand routing
- + - replicated route
E2:
Type of route. It can be one of the following values:
- * - Indicates the last path used when a packet was forwarded. It pertains only to the nonfast-switched packets. However, it does not indicate which path will be used next when forwarding a nonfast-switched packet, except when the paths are equal cost.
- E1 - OSPF external type 1 route
- E2 - OSPF external type 2 route
- IA - OSPF inter area route
- L1 - IS-IS Level 1 route
- L2 - IS-IS Level 2 route
- N1 - OSPF not-so-stubby area (NSSA) external type 1 route
- N2 - OSPF NSSA external type 2 route
10.110.0.0:
Indicates the address of the remote network.
[160/5]:
The first number in the brackets is the administrative distance of the information source; the second number is the metric for the route.
via 10.119.254.6:
Specifies the address of the next router to the remote network.
0:01:00:
Specifies the last time the route was updated (in hours:minutes:seconds).
Ethernet2:
Specifies the interface through which the specified network can be reached.
Code:
Router# <b class="cCN_CmdName">show ip bgp vpnv4 all<br />
</b>
Code:
BGP table version is 18, local router ID is 10.14.14.14<br />
Code:
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal<br />
Code:
Origin codes: i - IGP, e - EGP,? - incomplete<br />
Code:
Network Next Hop Metric LocPrf Weight Path<br />
Code:
Route Distinguisher: 1:101 (default for vrf vpn1)<br />
Code:
*>i10.6.6.6/32 10.0.0.21 11 100 0 ?<br />
Code:
*> 10.7.7.7/32 10.150.0.2 11 32768 ?<br />
Code:
*>i10.69.0.0/30 10.0.0.21 0 100 0 ?<br />
Code:
*> 10.150.0.0/24 0.0.0.0 0 32768 ?<br><br>BGP table version:<br>Internal version number of the table. This number is incremented whenever the table changes.<br><br>local router ID:<br>IP address of the router.<br><br>Status codes:<br>Status of the table entry. The status is displayed at the beginning of each line in the table. It can be one of the following values:<br>
- s - The table entry is suppressed.
- d - The table entry is dampened.
- h - The table entry history.
- * - The table entry is valid.
- > - The table entry is the best entry to use for that network.
- i - The table entry was learned via an internal BGP (iBGP) session.
Origin codes:
Origin of the entry. The origin code is placed at the end of each line in the table. It can be one of the following values:
- i - Entry originated from an Interior Gateway Protocol (IGP) and was advertised with a network router configuration command.
- e - Entry originated from an Exterior Gateway Protocol (EGP).
- ? - Origin of the path is not clear. Usually, this is a router that is redistributed into BGP from an IGP.
Network:
IP address of a network entity.
Next Hop:
IP address of the next system that is used when forwarding a packet to the destination network. An entry of 0.0.0.0 indicates that the router has some non-BGP routes to this network.
Metric:
If shown, the value of the interautonomous system metric.
LocPrf:
Local preference value as set with the set local-preference route-map configuration command. The default value is 100.
Weight:
Weight of the route as set via autonomous system filters.
Path:
Autonomous system paths to the destination network. There can be one entry in this field for each autonomous system in the path.
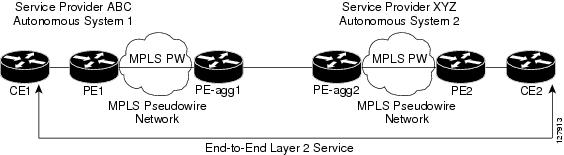
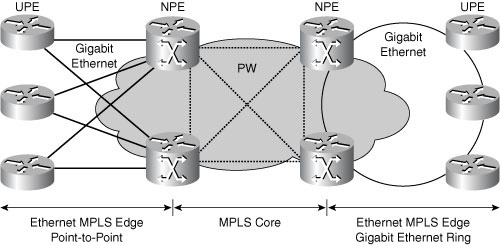
(n-1))/2, where n is the number of sites you need to connect. For example, if you need to have full-mesh connectivity between 4 sites, you will need a total of 6 point-to-point links or virtual circuits. To overcome this drawback and provide the customer with optimum data transport across the Service Provider backbone, the peer-to-peer VPN concept was introduced where the Service Provider actively participates in the customer routing, accepting customer routes, transporting them across the Service Provider backbone and finally propagating them to other customer sites.