PlAwAnSaI
Administrator
ENterprise designing and implementing Cloud Connectivity:

- enhanced Policy-Based Routing (ePBR) is used to direct packets that arrive at an interface to a specified next-hop. It is very useful in managing a large number of configured access lists more efficiently. In ePBR, router drops the traffic packets if the next hop configured in the PBR policy is not reachable. To avoid packet loss in such scenarios, must configure multiple next hops for each access control entry. Here are the steps to configure ePBR for IPv4 using Cisco vManage:
- Configure an extended ACL: This step involves defining the network or the host. For example, can permit IPv4 traffic from any source to specific hosts.
- Configure a class map that matches the ACL: Class maps match the parameters in the ACLs. For instance, can create a class map of type traffic and match it with the previously created ACL.
- Configure the policy map with the action to set the next hop: Policy maps with ePBR then take detailed actions based on the set statements configured. Can configure an ePBR policy map with the class map and set the next hop.
- Apply the service policy on the interface: Finally, apply the ePBR policy map to the interface. For example, can apply the policy map to a Gigabit Ethernet interface.
.
- Security groups are a feature in AWS that allow to control the inbound and outbound traffic to instances. They act as a virtual firewall that can filter the traffic based on the source, destination, protocol, and port. Can assign one or more security groups to instances, and each security group can have multiple rules. Security groups are stateful, meaning that they automatically allow the response traffic for any allowed inbound traffic, and vice versa. Security groups are essential for securing nodes in the AWS EKS cluster, as they can prevent unauthorized access to database or other resources. Can also use security groups to isolate nodes from other instances in the same VPC or subnet, or to allow communication between nodes in different clusters or regions.
- ExpressRoute is a service that provides a dedicated, private, and high-bandwidth connection between the customer's on-premises network and Microsoft Azure cloud network.
Private peering is a type of ExpressRoute circuit that allows the customer to access Azure services that are hosted in a virtual network, such as virtual machines, storage, and databases.
Secure Data Center Interconnect (SDCI) is a Cisco solution that enables secure and scalable connectivity between multiple data centers and cloud providers, using technologies such as MPLS, IPsec, and SD-WAN.
By using ExpressRoute with private peering and SDCI, the company can achieve the following benefits:- High availability: ExpressRoute circuits are redundant and resilient and can be configured with multiple service providers and locations for failover and load balancing. SDCI also provides high availability by using dynamic routing protocols and encryption mechanisms to ensure optimal and secure path selection.
- Redundancy: ExpressRoute circuits can be paired together to form a redundant connection between the customer's network and Azure. SDCI also supports redundancy by allowing multiple connections between data centers and cloud providers, using different transport technologies and service levels.
- Low latency: ExpressRoute circuits offer lower latency than public internet connections, as they bypass the congestion and variability of the internet. SDCI also reduces latency by using MPLS and SD-WAN to optimize the performance and quality of service for the traffic between data centers and cloud providers.
.
- To enable the OMP advertisement of BGP routes for a specific VRF instance on a Cisco IOS XE SD-WAN device, the engineer must first configure the global address-family ipv4 and then enable bgp advertisement under the vrf definition. This will allow the device to advertise the BGP routes learned from the cloud provider to the OMP control plane, which will then distribute them to the other SD-WAN devices in the overlay network.
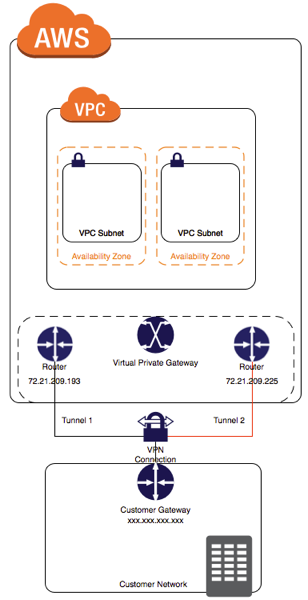
- An engineer needs to configure a site-to-site IPsec VPN connection between an on-premises Cisco IOS XE router and Amazon Web Services (AWS).
Two IP prefixes should be used to configure the AWS routing options are 20.20.20.0/24 & 40.40.40.0/24 because they are the IP prefixes that match the tunnel interfaces on the Cisco IOS XE router. The AWS routing options should include the local and remote IP prefixes that are used for the IPsec tunnel endpoints.Code:crypto keyring keyring-vpn-000001 pre-shared-key address 20.20.20.29 key awskey01 ! crypto keyring keyring-vpn-000002 pre-shared-key address 40.40.40.29 key awskey02 ! interface Tunnel1 ip address 30.30.30.29 255.255.255.252 tunnel destination 20.20.20.29 ! interface Tunnel2 ip address 30.30.30.33 255.255.255.252 tunnel destination 40.40.40.29 !
- The bgp advertise-best-external command is used to enable the advertisement of the best external path to internal BGP peers. This command is useful when there are multiple exit points from the local AS to other ASes, and the local AS wants to use the closest exit point for each destination. By default, BGP only advertises the best path to its peers, and the best path is usually the one with the lowest IGP metric to the next hop. However, this may not be the optimal path for traffic leaving the local AS, as it may result in suboptimal hot-potato routing or MED oscillations. The bgp advertise-best-external command allows BGP to advertise the best external path, which is the path with the lowest MED among the paths from different neighboring ASes, in addition to the best path. This way, the internal BGP peers can choose the best exit point based on the MED value, rather than the IGP metric.
Code:https://ithitman.blogspot.com/2015/04/configuring-cisco-bgp-best-external.html
- The process of configuring a Cisco SD-WAN Cloud Interconnect with Equinix involves several steps:

- This is the first step where ensure that there is the necessary UUIDs for the required number of Cisco SD-WAN Virtual Edge instances that want to deploy as Interconnect Gateways.
- After ensuring the availability of UUIDs, create the necessary network segments.
- After setting up the network segments, attach the Cisco SD-WAN Virtual Edge to the Equinix device template.
- Finally, create the Interconnect Gateway at the Equinix location that is closest to SD-WAN branch location.
.
- An engineer must redistribute IBGP routes into OSPF to connect an on-premises network to a cloud provider.
redistribute bgp 100 ospf 1 command redistributes the routes learned from BGP AS100 into OSPF Area 1, which allows router R3 to advertise those routes to router R2 and connect the on-premises network to the cloud provider.Code:https://github.com/ThaiCPE/encc/blob/main/README.md
- To redistribute OSPF internal routes into BGP:
R3# router bgp 100
redistribute ospf 1 > is used to redistribute OSPF routes from process ID 1 into BGP.
Last edited: